How would you feel if the White House ordered their insiders: David Plouffe, Sid Blumenthal, Robert Gibbs, David Axelrod, David Brock, Fusion GPS, Black Cube and the Denton Scumbag tabloids, to "end your life"?
"How can we prove that those people ordered and
financed those attacks against us? - Because we have the
emails, texts, financial records, whistle-blowers and other evidence
and because we were the only parties on Earth that were attacked by
those people, in those ways, at that time, right after we reported
their crimes to the authorities..."
The attacks, in bold red print,
below, were actually undertaken and documented against the
whistle-blower victims here.
POLITICAL KILL ORDERS AND STATE-SPONSORED CHARACTER
ASSASSINATIONS
How A Modern Character Assassination and Political "Kill Order" Is
Executed By the White House, their Silicon Valley Oligarchs and their
total control of propaganda media
Patrick George At Jalopnik attacks outsiders under contract with Elon
Musk and the DNC. Silicon Valley campaign finance oligarchs hire him to
run hatchet jobs on innocent outsiders and then Gawker-Gizmodo-Jalopnik
uses their financial partnership with the DNC's Google to push the
character assassination articles to the top of Google web products and
searches. Patrick George, Adrian Covert, John Hermann and Nick Cook are
the sexually degenerate cabin boys that report to boy-loving
sleaze-tabloid oligarch Nick Denton. They created the Fake News crisis
in the media by flooding the internet with defamation posts and reprisal
hatchet job articles designed to damage political enemies of the
Socialists. They coordinate a large number of the character
assassination efforts at Gawker, Gizmodo, Jalopnik, CNN, New York Times
and other propaganda outlets. These Millennial boys are "Media Rapists"
and should be treated as abusers.
How and why did a Donald Trump stripper-date named "Stormy" or an Elon
Musk sex party or a Kavanaugh drinking incident or the Moonves and
Weinstein indiscretions suddenly hit the news at about the same time in
news history?
In addition to actual murder, Politicians and Silicon Valley Oligarchs
hire operatives to end people's lives in other creative ways.
It is all part of the modern trend in vendetta, revenge and political
payback when a Senator or a tech oligarch issues a "kill order" on an
opponent.
The client does not like to get their hands dirty so the actual social
hit job is performed by companies such as: IN-Q-Tel - (DNC); Gawker
Media - PsyGroup - (DNC); (DNC); Jalopnik - (DNC); Gizmodo Media -
(DNC); K2 Intelligence - (DNC); WikiStrat - (DNC); Podesta Group -
(DNC); Fusion GPS - (DNC/GOP); Google - (DNC); YouTube - (DNC); Alphabet
- (DNC); Facebook - (DNC); Twitter - (DNC); Think Progress - (DNC);
Media Matters - (DNC); Black Cube - (DNC); Mossad - (DNC); Correct The
Record - (DNC); Sand Line - (DNC/GOP); Blackwater - (DNC/GOP); Stratfor
- (DNC/GOP); ShareBlue - (DNC); Wikileaks (DNC/GOP); Cambridge Analytica
- (DNC/GOP); Sid Blumenthal- (DNC); David Brock - (DNC); PR Firm
Sunshine Sachs (DNC); Covington and Burling - (DNC), Buzzfeed - (DNC)
Perkins Coie - (DNC); Wilson Sonsini - (DNC), David Plouffe Associates
(DNC), and hundreds of others…These are the people and companies
that except cash, revolving door jobs, political appointments, insider
trading stock in Silicon Valley tech companies, prostitutes and real
estate in exchange for destroying the lives of others.
These attackers deserve to be punished for the rest of their lives for
taking away the lives of others in exchange for cash. Any company who is
corrupt enough to hire any of these assassins should be forced out of
business. These attack services are responsible for 90% of the "Fake
News" problem in the world because they are the authors of most fake
news. Congress must act to make these kinds of companies illegal!
These digital assassination services offer hit-jobs, character
assassinations and economic reprisal programs to famous billionaires and
corrupt politicians who are seeking revenge, retribution and vendetta
executions. In the case of reporters getting targeted for attacks,
President Donald Trump has been accused by the liberal corporate media
of whipping up a hateful frenzy against the press. But while CNN’s Jim
Acosta grandstands against Trump, real journalists are still reeling
from the draconian extrajudicial measures that Barack Obama and his
administration used to target them for exposing truth.
This secretive targeting occurred while Obama speechwriter and
hate-filled ANTIFA supporter Ben Rhodes was running “Operation Echo
Chamber,” which reportedly continues, in which he fed information to
willing corporate media scribes. “They literally know nothing,” Rhodes
said of the twentysomething journalists he easily manipulated.
The Freedom of the Press Foundation’s Trevor Timm published documents
showing how former attorney general Eric Holder changed the rules to
more effectively intimidate and surveil members of the press.
Timm writes: “Today, we are revealing—for the first time—the Justice
Department’s rules for targeting journalists with secret FISA court
orders. The documents were obtained as part of a Freedom of Information
Act lawsuit brought by Freedom of the Press Foundation and Knight First
Amendment Institute at Columbia University.”
Trending: Brennan and Clapper Accused of Hacking John Roberts To
Blackmail Him
Obama is also clearly linked to the plot to obtain fraudulent FISA
warrants on President Trump’s team, as evidenced by Peter Strzok and
Lisa Page’s texts confirming that Obama was overseeing their
fly-by-night operation.
Larry Schweikart reported for Big League Politics:
For months pundits and researchers have been pondering the mystery of
the FISA approval that led to the illegal and historically titanic
scandals to ever hit the U.S. government. Some have argued that
Assistant Attorney General Rod Rosenstein knew the FISA was bogus when
he extended it. Others have wondered if Special Counsel Robert Mueller
knew about the fraudulent basis of the FISA when he used it, in part, to
indict Michael Flynn. Other still, that Mueller was fooled by the FBI.
This is what President Trump calls “SPYGATE”.
It may well be that the surveillance that was conducted began with UK
intelligence services and then was fed back to the White House of Barack
Obama. Here’s the kicker:
President Barack Obama did not need a FISA warrant to authorize
spying/electronic surveillance on Trump because Obama all along had
legal authorization to by-pass the normal court vetting process.
According to 50 U.S. Code 1802, the “Electronic Surveillance
Authorization” () “Foreign intelligence in relation to a US person
(Trump or his associates) is information that’s necessary for the US to
protect against attack, hostile acts, sabotage, . . . as well as other
clandestine activities by a foreign power . . . OR . . . information
relevant to national defense/security of the US, or the conduct of
foreign affairs of the U.S.” Such an authorization by Obama required
certification by Attorney General Loretta Lynch that must be logged with
the FISC court. (“The [AG]+ shall immediately transmit under seal to the
court [FISC] a copy of his certification.”)
In short, the DOJ has this. If we are correct, a copy of that
certification is currently under seal at least with the DOJ and the
FISC.
This is what they are hiding.
However, the Act requires the AG to keep the Select Committee on
Intelligence and the Senate Committee on Intelligence informed of these
authorizations and unmaskings therein. See 1803 (a) (1) (C) If indeed
this is what happened, did Lynch report—or only selectively report—to
the committees in a way that excluded non-friendlies? Can you see why
Adam Schiff, Mark Warner, and their ilk are terrified?
1) Obama authorized spying/electronic surveillance on Team Trump,
by-passing normal judicial oversight.
2) To create “foreign intelligence,” John Brennan and others organized
for UK intelligence to conduct surveillance on Trump and his associates,
either from the UK or from UK assets within the U.S. This is another
reason revealing this will unleash an excrement storm: the UK is about
to be caught meddling bigly in an American election.
3) Lynch certified Obama’s authorization which is now held under seal by
DOJ (and FISC).
From this authorization, all unmaking followed, as well as the FBI
fraudulent counter intel investigation and perhaps the FISA warrant too.
Obama knew this was all fake when he made the authorization; Lynch knew
it was fake when she certified it; the entire inner circle, including
the FBI, all knew. This takes the U.S. into uncharted territory, and
could imperil any politician in the British government who supported
this or had knowledge of it. Proving any of this would be difficult, as
if confronted Lynch would almost certainly cover up and Obama would
simply deny knowledge. Without a paper trail, a conviction might be a
bridge too far. This is only one of thousands of "kill order" tactics
introduced by the Obama Administration.
------------------------------
These are the playbook tactics
that The White House, Senators and tech oligarchs used to destroy
the lives of their political and business enemies who are the
victims herein:
-
Government agency bosses solicited the target victims with false
promises of future loans, contracts or grants from their agency
and caused the target victims to expend millions of dollars and
years of their time for projects which those government bosses had
covertly promised to their friends. They used the target victims
as a “smokescreen” to cover their illegal government slush-funds
(Ie: Department of Energy programs and DOT "Autopilot cars") for
the victims competitors and personal enemies. By using this
tactic, the attackers drain the target victims funds and force
them into an economic disaster in plain view of everyone without
the government bosses fearing any reprisal for their scam.
- Every match.com, okcupid.com, Plenty Of Fish,
Seeking Arrangements and all other IAC-owned, or similar, dating
sites (IAC is managed by Hillary Clinton's daughter) have had
their profiles, texts, and inter-member communications, since
those companies were started, hacked or purchased. The attack
service providers use Palantir and In-Q-Tel financed data analysis
software to analyze every activity in those dating services in
order to find honey-trap, blackmail, sextortion and social
conflict exploitation opportunities. If you had a bad date with
someone, that someone will be hunted down and convinced to help
harm, #metoo or "rape charge" the intended target. All dates
involve a search for sex, so the likelihood that a sexual
disappointment experience will exist in each persons dating
history is high. Searching every past dating email and text of a
subject is quite easy with modern software and hacking techniques.
A synthetically amplified, PR-agency optimized sex scandal can
destroy any target. Your dating experiences from the 70's or 80's
will come back to haunt you decades later. Most dates involve
drinking alcohol and taking drugs. If you were unattractive or had
bad sexual skills your bad date will be called "date rape",
"drugging your date for sex" and related twisted narratives that
are designed to shame you, the target. If you try to get a date in
the future, your potential date will be contacted by a third party
who will slander and libel you to make sure your potential first
date gets cancelled. Your social life will, essentially, end.
Every photo on every dating site is cross checked with every other
photo on the internet in order to cull your Facebook, Linkedin,
Snapchat and other social media together to create a total
psychological manipulation profile data file on you. A single
photo on a dating site can be cross searched on every mugshot
archive, photo album and corporate database in the worth within
minutes using modern super-computers. Your sex life will be on
public record in a flash.
- Social Security, SSI, SDI, Disability and
other earned benefits were permanently stone-walled. Applications
of targets were “lost”. Files in the application process
“disappeared”. Lois Lerner hard drive “incidents” ( https://en.wikipedia.org/wiki/IRS_targeting_controversy )are operated in order to seek to hide
information and run cover-ups in order to run state-sponsored
attacks on whistle-blowers.
- Government officials and tech oligarchs
contacted members of the National Venture Capital association
(NVCA) and created national “black-lists” to blockade target
victims from ever receiving investor funding. This was also
confirmed in a widely published disclosure by Tesla Motors Daryl
Siry and in published testimony. When Silicon Valley political
campaign finance oligarchs and their White House insiders
black-list you (see the "AngelGate" Scandal and the "Silicon
Valley High Tech No Poaching Class Action Lawsuit" cases) you will
never get investor funding again.
- Victim's FOIA requests were hidden, frozen,
stone-walled, delayed, lied about and only partially responded to
in order to seek to hide information and run cover-ups.
- State and federal employees at agencies have
played an endless game of Catch-22 by arbitrarily determining that
deadlines had passed that they, the government officials, had
stonewalled and obfuscated applications for, in order to force
these deadlines that they set, to appear to be missed. This can
bankrupt a target victim.
- Some Victims found themselves strangely
poisoned, not unlike the Alexander Litvenko case. Heavy metals and
toxic materials were found right after their work with the
Department of Energy weapons and energy facilities. Many wonder if
these targeted former federal employees and contractors were
intentionally exposed to toxins in retribution for their
testimony. The federal MSDS documents clearly show that a number
of these victims were exposed to deadly compounds and radiations,
via DOE, without being provided with proper HazMat suits which DOE
officials knew were required. California laws say that the victims
were "employees" yet the federal agencies they worked for kept
trying to call them "contractors" in order to stave off liability.
Poisoning whistle-blowers is an age old political practice
undertaken by executive officers in State agencies like the D.O.E.
- Victims employers were called, and faxed, and
ordered to fire targeted victims from their places of employment,
in the middle of the day, with no notice, as a retribution tactic.
No legal reason for the firings was ever supplied to the victims.
- On orders from Obama White House officials,
DNC-financed Google, YouTube, Gawker Media and Gizmodo Media
produce attack articles and defamation videos. DNC-controlled
Google locked these attack articles and movies on the internet on
the top line, of the front page of all Google and Youtube searches
for a decade in front of 7.5 billion people, around the world.
This attack-type uses over $40 million dollars in server farms,
production costs and internet rigging. The forensic data acquired
from tracking some of these attacks proves that Google rigs
attacks against individuals on the internet and that all of
Google’s “impressions” are manually controlled by Google’s
executives who are also the main financiers and policy directors
of the Obama Administration. This data was provided to the
European Union for it’s ongoing prosecution of Google’s political
manipulation of public perceptions.
- Victims HR and employment records, on
recruiting and hiring databases, were embedded with false negative
keywords and coded "red flags" in order to prevent the victim
targets from ever gaining future employment. These hacking-like
tactics were so sophisticated that only a state-sponsored group
could have undertaken such attacks!
- Gary D. Conley, Seth Rich, Rajeev Motwani,
Micheal Hastings and many other whistle-blowers in these matters,
turned up dead under strange circumstances. It is very possible
that some of these attack services, operated by former CIA
operatives, offer discrete murder-for-sale services using
high-tech assassination tools that make murders look like heart
attacks and organ failures.
- Disability and VA complaint hearings and
benefits were frozen, delayed, denied or subjected to lost records
and "missing hard drives" as in the Lois Lerner case.
- Paypal (A DNC-biased operation) and other
on-line payments for on-line sales were de-platformed, delayed,
hidden, or re-directed in order to terminate income potential for
target victims who competed with the attackers interests and
holdings.
- Web server global DNS redirection, "website
spoofing" sent target victims websites to dead ends where no sales
orders or customer inquiries actually get back to the target
victim. These internet revenue activity manipulations are
conducted using Google and Amazon servers. All commercial
storefronts and on-line sales attempts by target victims, will
have had their sites hidden, or search engine de-linked by a
massively resourced facility located in Virginia, Texas or Palo
Alto, California in order to terminate revenue potentials for the
target victims.
- Thousands of hired "trolls", "blogger
shills", "botnets" and "synth-blog" deployments were deployed to
place defamatory statements and disinformation about victims in
front of 7.5 billion people around the world on the internet in
order to seek to damage their federal testimony credibility by a
massively resourced facility. Many of these click-farms and shill
farms are located off-shore but the payments to them, for the
attack services, track back to White House contractors and
financiers.
- Campaign finance dirty tricks contractors
were hired by campaign financiers to attack the friends and family
members of the target victims in order to create low morale for
the target victims psyche and motivation.
- Electronic attack devices were placed in
nearby vehicles and apartments located close to victims. The U.S.
Government has now acknowledged that the Cuban, Chinese and other
embassy "sonic attacks" are from a known microwave beam weapon.
Any one of the technical departments of the attack services listed
at the top of this article can build such a biological harassment
weapon. It can be aimed at the target victims office, bedroom or
vehicle and, within a week, have caused biological and emotional
damage using a weapon that has no visible track of trajectory. It
is designed to make the target victim think they are "going crazy"
or "hearing sounds in their head". While this may sound pretty
wild, web search "Embassy sonic attacks" on the top 5 non-Google
search engines and read the very credible reports of these
attacks.
- In one case covert political partner: Google,
transferred large sums of cash to dirty tricks contractors and
then manually locked the media portion of the attacks into the top
lines of the top pages of all Google searches globally, for years,
with hidden embedded codes in the links and web-pages which
multiplied the attacks on Victims by many magnitudes.
- The U.S. Patent Office was used as a weapon
against victims who had inventions. Covert Cartel financier:
Google, placed Google’s lawyer: Michelle Lee, in charge of the
U.S. Patent Office and she, in turn, stacked all of the U.S.
Patent Office IPR and ALICE review boards and offices with
Google-supporting employees in order to rig the U.S. Patent Office
to protect Google from being prosecuted for the vast patent thefts
that Google engages in. Google has hundreds of patent lawsuits for
technology theft and a number of those lawsuits refer to Google’s
operations as “Racketeering”, “Monopolistic Cartel” and
“Government Coup-like” behaviors. Thousands of articles and
investigations detail the fact that Google, “essentially” ran the
Obama White House and provided over 80% of the key White House
staff. A conflict-of-interest unlike any in American history.
Google’s investors personally told Applicant they would “kill
him”. Google and the Obama Administration were “the same entity”.
Applicant testified in the review that got Michelle Lee terminated
and uncovered a tactical political and social warfare group inside
Google who were financed by Federal and State funds.
- Honeytraps and moles were employed by the
attackers. In this tactic, people who covertly worked for the
attackers were employed to approach the “target” in order to spy
on and misdirect the subject.
- Gawker Media, Gizmodo Media, Snopes, SPLC and
other hired media assassins were retained to produce "hatchet job"
character assassination articles about victims. Then those
articles were faxed, mailed and emailed to the employers and
investors of victims with a note saying: "You don't want to have
anything to do with this person, do you..?" in order to get
victims fired from their job and get their loans or financing
pulled. The attackers used the attack media, that they authored,
to create an attack designed to end victim's lives via economic
warfare.
- Mortgage and rental applications for victims
had red flags added to them in databases to prevent the targets
from getting homes or apartments.
- Krebs On Security, Wired, Ars Technica, The
Wall Street Journal and most major IT publications have reported
that hundreds of spy "back-doors" have been found on every Intel,
AMD, Apple, Xfinity, Cisco, Microsoft, Juniper Networks
motherboard, chip-set and hardware component set. This means that
any kid with the "key" code can open any computer, server, router,
cloud-network or other network connected device and read every
file, photo, video, your calendar and email on your devices at any
time from any location on Earth. The key codes have been released
to every hacker community in the world for over ten years. There
is now no government, corporate or personal data that can't be
hacked, even data from decades ago. Every single one of your
darkest secrets can be in the hands of your enemy within 60
minutes, or less. Important meetings you had planned with
potential investors, employers, clients, dates, suppliers and
others will suddenly get cancelled at the last minute. They will
get cancelled because your enemies are reading your calendar
remotely and covertly sending slander information to those you had
hoped to engage with in order to sabotage your life. Nothing you
have ever typed on a computer or Smartphone is safe. it WILL be
acquired and it WILL be used against you. This WAS DONE to the
victims by a sophisticated hacking effort.
- McCarthy-Era type "Black-lists" were created
and employed against target victims who competed with Obama
Administration executives and their campaign financiers to prevent
them from getting funding and future employment.
- The victims were very carefully manipulated
into a position of not being able to get jobs, unemployment
benefits, disability benefits or acquire any possible sources of
income. The retribution tactics were audacious, overt..and quite
illegal.
- There are thousands of additional Dirty
Tricks tactics being used by these Attack Services yet Congress
refuses to pass laws out-lawing such attack services. The cost of
an attack on a person ranges from $150,000.00 to over
$50,000,000.00. While a Silicon Valley billionaire can afford to
launch counter-measures to these attacks, any regular taxpayer
will be utterly destroyed, and incapable of fighting back, against
even the smallest version of one of these "kill orders". A number
of modern office shootings are the results of these attacks
against an individual who has lost everything because of the
attack and has no options left.
--------------------------------------------------
Federal law enforcement, the United States Congress and the highest
level investigators in the U.S., and abroad, have documented (per the
“FISA Memo”, Congressional Reports and federal employee testimony) and
proven the fact that the Obama Administration regularly engaged in the
operation of retribution, vendetta and reprisal campaigns known as
“hit-jobs” against domestic natural born U.S. citizen domestic
taxpayers. The Federal Court, in at least one previous court case,has
ruled that Applicants, in this particular matter, were the victims and
target of a number of these attacks designed to inflict permanent
medical, emotional, character assassination, brand negation, economic
and career damage.
'They Can't Beat Him On The Law So They Are Trying To Destroy His Life'
-Sen. Graham Questions Dems' Motives On Brett Kavanaugh Sexual Assault
Allegations (dailycaller.com)
LINKS TO PROOF OF THESE ATTACK DEPLOYMENTS THAT WILL STAND UP IN
COURT:
http://www.google-is-a-mobster.com
http://www.londonworldwide.com
https://bigleaguepolitics.com/brennan-and-clapper-accused-of-hacking-john-roberts-to-blackmail-him/
https://bigleaguepolitics.com/heres-why-obama-clearly-ordered-the-spying-on-trump/
https://dailycaller.com/2018/09/17/lindsey-graham-dems-kavanaugh/
https://www.politico.com/gallery/16-worst-political-dirty-tricks
http://artofverbalwar.com/2016/11/03/quick-dirty-guide-political-debate-tactics/
https://politicaldictionary.com/topics/dirty-tricks/
https://www.learntoinfluence.com/dirty-tricks-and-office-politics/
https://www.motherjones.com/politics/2012/11/election-dirty-tricks/
https://www.nytimes.com/2016/10/21/us/politics/video-dnc-trump-rallies.html
https://en.wikipedia.org/wiki/Ratfucking
http://www.electomatic.com/dirty-campaign-techniques/
https://en.wikipedia.org/wiki/COINTELPRO
https://www.cnn.com/2008/POLITICS/05/29/obamas.first.campaign/
https://whyy.org/articles/political-dirty-tricks-are-a-staple-of-modern-politics/
https://www.reddit.com/r/dredmorbius/comments/2d0r1d/the_reactionary_political_debate_playbook_karl/
https://www.politico.com/story/2016/02/south-carolina-dirty-tricks-republicans-219116
https://www.youtube.com/watch?v=VP5jqLAjbDw
!!!!! Mueller Hears That Silicon Valley Has Been Manipulating
The Entire BREXIT Campaign using covert Opposition tactics
!!!!!!
- Second former employee of controversial data firm to be questioned by
special counsel’s inquiry into Russia collusion
By Carole Cadwalladr
Brittany Kaiser is said to be cooperating fully with the Mueller
inquiry.
A director of the controversial data company Cambridge Analytica, who
appeared with Arron Banks at the launch of the Leave.EU campaign, has
been subpoenaed by the US investigation into possible collusion between
the Trump campaign and the Russian government.
A spokesman for Brittany Kaiser, former business development director
for Cambridge Analytica – which collapsed after the Observer revealed
details of its misuse of Facebook data – confirmed that she had been
subpoenaed by special counsel Robert Mueller, and was cooperating fully
with his investigation.
He added that she was assisting other US congressional and legal
investigations into the company’s activities and had voluntarily turned
over documents and data.
Kaiser, who gave evidence to the UK parliament last April in which she
claimed Cambridge Analytica had carried out in-depth work for Leave.EU,
is the second individual connected to the firm subpoenaed by the special
counsel. The Electoral Commission has said its investigation into
Leave.EU found no evidence that the campaign “received donations or paid
for services from Cambridge Analytica …beyond initial scoping work”.
Damian Collins, chairman of parliament’s inquiry into fake news, said it
was “no surprise” that Kaiser was under scrutiny by Mueller because “her
work connected her to WikiLeaks, Cambridge Analytica and [its parent
company] SCL, the Trump campaign, Leave.EU and Arron Banks”.
He said it was now vital Britain had its own inquiry into foreign
interference: “We should not be leaving this to the Americans.”
Tom Watson, the deputy leader of the Labour party, echoed Collins’s
statement, saying: “This is the first evidence that a significant player
in the Leave.EU campaign is of interested to the global Mueller inquiry.
People will be bewildered that the British government has no interest in
establishing the facts of what happened.”
In August, Sam Patten, a US political consultant who had worked for
Cambridge Analytica on campaigns in the US and abroad, struck a plea
deal with Mueller after admitting he had failed to register as a foreign
agent for a Ukrainian oligarch.
He became a subject of the special counsel’s inquiry because of work
done with Paul Manafort, Trump’s campaign manager, in Ukraine. He had
also set up a business with Konstantin Kilimnik, a key figure who
Mueller has alleged has ties to Russian intelligence and who is facing
charges of obstruction of justice. In a 2017 statement to the Washington
Post, Kilimnik denied any connection to intelligence services. Kaiser,
however, is the first person connected directly to both the Brexit and
Trump campaigns known to have been questioned by Mueller.
The news came to light in a new Netflix documentary, The Great Hack,
which premiered at the Sundance film festival last month and is expected
to be released later this spring. Film-makers followed Kaiser for months
after she approached the Guardian, including moments after she received
the subpoena. She claims the summons came after the Guardian revealed
she had visited WikiLeaks founder Julian Assange while still a Cambridge
Analytica employee in February 2017, three months after the US election.
One part of Mueller’s investigation focuses on whether the Trump
campaign sought to influence the timing of the release of emails by
WikiLeaks before the election. Investigators are looking at
communications between them. In the film, Kaiser says that she has gone
from being a cooperating witness to a subject of investigation because
of her contact with Assange.
In October 2017, it was revealed that Alexander Nix, the chief executive
of Cambridge Analytica, had contacted Assange in August 2016 to try to
obtain emails from Hillary Clinton’s presidential campaign – which
indictments from Mueller’s team say were obtained by Russian military
intelligence – to use in Donald Trump’s campaign. When Kaiser gave
evidence to parliament last year, she was asked about her relationship
with Assange and WikiLeaks but failed to reveal that she had met
Assange.
In the documentary, Kaiser is shown after receiving an email from the
Guardian last June asking about meeting Assange and alleged donations of
cryptocurrency to WikiLeaks. Kaiser did not respond to the email at the
time, but on camera says: “She knows I met Assange. And she knows I
donated money to WikiLeaks in bitcoin.”
Her legal representatives later wrote to the paper to say that the
allegations, including that she had “channelled” donations to WikiLeaks,
were false. Kaiser said she had received a small gift of bitcoin in 2011
– long before she worked at Cambridge Analytica – and, not knowing what
else to do with it, gave it to WikiLeaks, because she had benefited from
material it had released over the years.
Her lawyer told the Observer that the meeting with Assange came about
after a chance encounter in London with an acquaintance who knew him. It
lasted 20 minutes and consisted mainly of Assange telling her “about how
he saw the world”. He said they did not discuss the US election.
Patten and Kaiser were involved in a controversial election campaign in
Nigeria in January 2015, which former Cambridge Analytica employees say
had “unsettling” parallels to the US presidential election.
The Guardian revealed that the data firm had worked alongside a team of
unidentified Israeli intelligence operatives on the campaign.
Ex-Cambridge Analytica employees described how the Israelis hacked the
now-president of Nigeria’s emails and released damaging information
about him to the press weeks before the election.
=====================
CBS NEWS 60 MINUTES Lara Logan "I’m Being ‘Targeted’ For Saying
the Media is ‘Mostly Liberal"
by Tamar Auber
On Wednesday, former CBS News foreign correspondent Lara Logan spoke
with Fox News Sean Hannity about her recent comments slamming the media
as “mostly liberal.”
Logan told Breitbart podcaster Mike Ritland the remarks made on his show
— which drew widespread attention online — amounted to “professional
suicide.”
Defending her remarks on Hannity’s show, Logan said that as the result
of her speaking out about how the media is “mostly liberal” she has been
targeted because she is an independent voice.
“Any journalists who are not beating the same drum and giving the same
talking points,” she insisted “pay the price” for not going along with
the liberal crowd.
She also called out her targeters by name.
“I know they’re going to come after me,” she told Hannity. “Michael
Calderone who is at the Huffington Post. I can give you the script now.
I can tell you who the players are. Joe Hagan. Brian Stelter.”
She added: “They smear you personally. They go after your integrity.
They go after your reputation as a person and a professional. They will
stop at nothing. I am not the only one. And I am just, I am done, right,
I am tired of it. And they do not get to write my story anymore. They
don’t get to speak for me, I want to say loudly and clearly to anybody
who is listening, I am not owned. Nobody owns me, right? I’m not owned
by the left or the right.”
Logan made headlines recently when, during a scorched earth podcast
interview with Ritland, she said that there was a lot of “weight” in
most news organizations on “one side of the political spectrum.”
“The media everywhere is mostly liberal. But in this country, 85 percent
of journalists are registered Democrats. So that’s just a fact, right?”
she told Ritland.
She also trashed reporting based on single, anonymous government
sources.
“That’s not journalism, that’s horseshit,” Logan stressed.
“Responsibility for fake news begins with us. We bear some
responsibility for that, and we’re not taking ownership of that and
addressing it. We just want to blame it all on somebody else.”
=================================
MEET THE ATTACKERS CALLED: Psy-Group
Internal documents from a private Israeli intelligence firm called
Psy-Group show that, at the time of many incidents, the company, and
possibly other private investigators, were targeting U.S. citizens
because they spoke up about crimes.
Psy-Group’s intelligence and influence operations, which included a
failed attempt in the summer of 2017 to sway a local election in central
California, were detailed in a New Yorker investigation that I co-wrote
earlier this month. Before it went out of business (ie: changed it's
name) , last year, Psy-Group was part of a new wave of
private-intelligence firms that recruited from the ranks of Israel’s
secret services and described themselves as “private Mossads.” Psy-Group
initially stood out among its rivals because it didn’t just gather
intelligence; its operatives used false identities, or avatars, to
covertly spread messages in an attempt to influence what people believed
and how they behaved. In 2016, Psy-Group held discussions with the Trump
campaign and others about conducting covert “influence” operations to
benefit the candidate. Psy-Group’s founder and C.E.O., Royi Burstien, a
veteran Israeli intelligence officer who established the firm in 2014,
told me that his talks with the Trump campaign went nowhere. The
company’s posturing, however, attracted the attention of Robert Mueller,
the special counsel, who has been investigating interference in the 2016
Presidential race.'
Silicon Valley oligarchs have over 100 different Psy-Group type attack
services to choose from!
================================
FED BOMBSHELL: Fusion GPS Bribed Dozens of MSM Journalists With
Cash To Run Character Assassinations, While News Companies Paid Firm
to Dig Dirt on Trump
High-ranking FBI insiders are pulling back the curtain on Fusion GPS,
the firm that commissioned and spread the bogus Trump dossier.
It appears the embattled intelligence firm was quite busy paying off Big
Media reporters, according to federal sources who have traced dozens of
transactions between TD Bank and media members as well as media
organizations, sources confirm.
But stunningly, Big Media organizations have employed Fusion GPS to dig
dirt on politicians and D.C.’s elite — namely Donald Trump.
“Fusion GPS was on the payroll of the media and in turn had members of
the media on its payroll,” one FBI insider said.
Bombshell revelations.
FBI insiders confirm Fusion GPS employed law firms as well as shell
companies to send and receive funds to and from media and reporters. But
the embattled firm also used its accounts at TD Bank to directly
commission reporters. Likewise, Fusion GPS received funds from media
companies into its own accounts at TD Bank, FBI insiders said,
“There are dozens of payments from the media flowing into their (Fusion
GPS’) account,” one federal law enforcement official said. “One company
wired funds to Fusion (GPS) more than a dozen times.”
Why would media companies commission Fusion GPS? Likely to dig dirt on
enemies or secure records that reporters could not legally obtain, one
federal law enforcement insider said. One FBI insider said the payments
to Fusion GPS coincide with Donald Trump’s run for the White House.
The payments were made between Sept. 2015 and Sept. 2017, records show.
The unthinkable: The mainstream media paying Fusion GPS for dirt on
Trump to the same firm the Democratic National Committee paid to fund
the bogus Trump dossier. And at the same time Fusion GPS bribing
journalists to place stories — likely negative about Trump, as well as
spread the bogus Trump dossier around.
Stunning.
Was Buzzfeed — the only company to publish the full bogus dossier — on
that list?
And who is on the payroll? We are trying to run that information down.
And why aren’t these people behind bars?
The California DMV Is Making $50M a Year Selling Drivers’ Personal Information To Your Enemies
A document obtained by Motherboard shows how DMVs sell people’s names, addresses, and other personal information to generate revenue.
Image: Mark Boster/Los Angeles Times via Getty Images
The California Department of Motor Vehicles is generating revenue of $50,000,000 a year through selling drivers’ personal information, according to a DMV document obtained by Motherboard.
DMVs across the country are selling data that drivers are required to provide to the organization in order to obtain a license. This information includes names, physical addresses, and car registration information. California’s sales come from a state which generally scrutinizes privacy to a higher degree than the rest of the country.
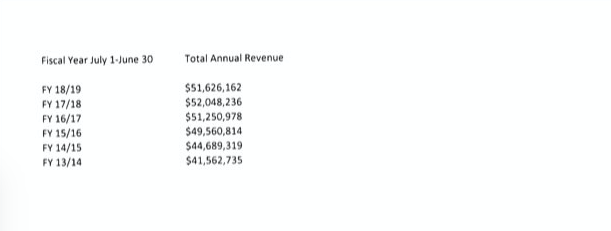
In a public record acts request, Motherboard asked the California DMV for the total dollar amounts paid by commercial requesters of data for the past six years. The responsive document shows the total revenue in financial year 2013/14 as $41,562,735, before steadily climbing to $52,048,236 in the financial year 2017/18.
The document doesn't name the commercial requesters, but some specific companies appeared frequently in Motherboard's earlier investigation that looked at DMVs across the country. They included data broker LexisNexis and consumer credit reporting agency Experian. Motherboard also found DMVs sold information to private investigators, including those who are hired to find out if a spouse is cheating. It is unclear if the California DMV has recently sold data to these sorts of entities.
In an email to Motherboard, the California DMV said that requesters may also include insurance companies, vehicle manufacturers, and prospective employers.
Asked if the sale of this data was essential to the DMV, Marty Greenstein, public information officer at the California DMV, wrote that its sale furthers objectives related to highway and public safety, "including availability of insurance, risk assessment, vehicle safety recalls, traffic studies, emissions research, background checks, and for pre- and existing employment purposes."
"The DMV takes its obligation to protect personal information very seriously. Information is only released pursuant to legislative direction, and the DMV continues to review its release practices to ensure information is only released to authorized persons/entities and only for authorized purposes. The DMV also audits requesters to ensure proper audit logs are maintained and that employees are trained in the protection of DMV information and anyone having access to this information sign a security document," Greenstein wrote.
Do you know anything else about data selling? We'd love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
Multiple other DMVs around the U.S. previously confirmed to Motherboard that they have cut-off data access for some commercial requesters after they abused the data.
One of the main pieces of legislation that governs the sale of DMV data stemmed from a case in California. Lawmakers introduced the Driver's Privacy Protection Act (DPPA) in 1994 after a private investigator hired by a stalker obtained the address of actress Rebecca Schaeffer from the DMV. The stalker went on to kill Schaeffer. The DPPA was designed to restrict access to DMV data, but included a wide array of exemptions, including for private investigators.
After Motherboard's earlier investigation, senators and digital privacy experts criticized the sale of DMV data, and some said the law should be changed. Senator and Democratic Presidential candidate Bernie Sanders said DMVs should not profit from such information.
What Is Opposition Research? Understanding the Dirty Tactics Used By Obama ...
Opposition research: When is the right time for a campaign to ...
Democrats' opposition research got exposed — this time, not ...
Russian government hackers penetrated DNC, stole opposition ...
Section 1. Overview of Opposition Tactics: Recognizing the ...
Russian Government Hackers Penetrated DNC, Stole Opposition ...
Opposition Research | Definition of Opposition Research by Lexico
Here's the leaked opposition research document on Donald ...
An Introduction To The Dark Arts Of Opposition Research That DNC Execs Use ...
The party is now publicly attacking progressive ...
The DNC's Facebook used opposition-research firm to link political critics to ...
Attack ad - Wikipedia
THE SPIES THAT POLITICIANS AND OLIGARCHS HIRE TO END YOUR LIFE - "THEY SENT THEM AFTER ME!"
- Stella Penn Pechanac worked for a Mossad-linked Israeli intelligence company
- Weinstein hired the firm just months before sexual allegations ruined his career
- But Stella told the actress she was executive at London asset management firm
With her long blonde hair, catwalk figure and dazzling smile, it's easy to believe that Stella Penn Pechanac could have been one of the victims of disgraced Hollywood mogul Harvey Weinstein.
Indeed, that's exactly what she told New York Magazine writer Ben Wallace when she introduced herself as 'Anna' with another terrible story about the influential producer.
However, with his journalist's instinct, Wallace smelled a rat.

Stella Penn Pechanac (pictured) was a spy working for the infamous Mossad-linked Israeli intelligence company Black Cube
This was 2016, well before the #MeToo scandal emerged, and even Wallace's colleagues had no idea he was investigating claims of sexual harassment against Weinstein.
When they met for coffee, 'Anna' confided she had had an affair with Weinstein that had ended badly.
But there was something about her story that didn't quite ring true. She seemed far more concerned, in fact, with asking questions about other Weinstein victims than her own story.
Call it paranoia, but Wallace had a sneaking suspicion she was recording him.
However, Rose McGowan, the actress who first accused Weinstein of rape, was rather more easily fooled.
Stella's plausible manner and hard-to-place European accent convinced the actress that she was Diana Filip, an executive from London asset management firm Reuben Capital Partners, who wanted to invite McGowan to speak at a gala dinner.

She befriended actress Rose McGowan (alongside Harvey Weinstein in 2007) after telling her that she was an executive from a London asset management firm who wanted to invite her to speak at a gala dinner
They met for long walks, drinks and girls' nights out. McGowan even told her 'there was no one else in the world she could trust'.
But it was all a con. Just like Anna, Diana was merely a cover dreamed up by Stella, a spy working for the infamous Mossad-linked Israeli intelligence company Black Cube.
Weinstein had hired the firm in the months before his career and reputation were ruined by a welter of sexual allegations.
An extraordinary contract, dated July 11, 2017, between the mogul's lawyers and the British arm of the Israeli firm show that Weinstein had tasked Black Cube with two primary objectives: to 'provide intelligence which will help the Client's efforts to completely stop the publication of a new, negative article in a leading NY newspaper', and to 'obtain additional content of a book which is currently being written and which includes harmful negative information on and about the Client'.
To achieve this, Black Cube promised a dedicated team. As part of the operation, codenamed Parachute, the organisation introduced Stella to Weinstein.
Her main objective was to befriend McGowan, obtain a draft of her memoir – and discredit it. And she was tasked with finding out about and blocking other allegations about Weinstein – just like the stories Ben Wallace was working on.

Stella, now 36, went undercover to meet a worker in a bank that had been critical of a Black Cube client but she has since turned her back on the world of espionage
In late 2017, Weinstein met three Black Cube operatives in the back room of a New York restaurant. There, one of the agents told Weinstein 'we got something good for you'.
After a short pause, a woman with long blonde hair and high cheekbones stepped forward and introduced herself as Anna.
She read passages from McGowan's upcoming book. Listening in a state of shock, Weinstein muttered repeatedly: 'Oh my God.'
Today, Stella Penn Pechanac has left her lucrative job at Black Cube and claims to have turned her back on the murky world of espionage.
She is pregnant with her second child and, in an exclusive interview with The Mail on Sunday, has agreed to lay bare her extraordinary and disturbing double life as an agent for hire.
It is clear from the first moment that Stella is ideal spy material. She comes across as open, engaging and honest, with an unwavering gaze and a seemingly puncture-proof self-confidence.
The first thing she wants to make clear is that she was never involved in any honeytraps.
'I was never a Bond girl,' she insists.
'I was James.'
So how did she come to be a central figure in the most explosive scandal ever to grip Hollywood?
'I acted for years, I spoke five languages, and I travelled a lot,' she says.
'They approached me.'
If that seems unlikely, consider that Black Cube was set up by former Israeli intelligence officers in 2010 and is known for – and trades on – its links with the feared Mossad intelligence service.
Consider also that Stella's fractured background could have been dreamed up by John le Carré: she was born in Sarajevo into a mixed Muslim/Orthodox Christian family that had sheltered Jewish Yugoslavs during the Holocaust. Her grandfather perished in a concentration camp.
Her family converted to Judaism and escaped the bloody Balkans civil war in 1994 and Stella volunteered for the Israeli Defence Force as soon as she turned 18, rising to lieutenant in the air force.
She graduated from an elite Israeli university and went to drama school before joining Black Cube. Although there appear to be puzzling gaps in her CV, she doesn't admit to any previous intelligence training.
However, she did divulge it was the ex-Israeli premier Ehud Barak who put Weinstein's lawyers in touch with the firm.
'The company received the project, examined it, found it legitimate,' Stella says.
'Weinstein was respected, everyone wanted to work for him, with him. We had this new project, it was like a big deal, a huge client coming in. He was facing serious allegations, and there were suspicions there was a negative campaign against him.
'I've worked on cases like this before so it was just another of those, a commercial negative campaign but on a much bigger scale because of Weinstein.'
Stella, 36, is eager to stress that Black Cube field agents usually do not meet the clients, but in this case Weinstein insisted on seeing her face-to-face. The initial meeting, she says, gave her a rare insight into the disgraced titan.
'He was 100 per cent sure people were out to get him,' she says.
'So when I met him, contrary to the huge reputation he had – how powerful, strong, dominant he had been portrayed – he was vulnerable.
'He was saying, 'Someone out there is trying to get me, I need your help and everything they are saying is a bunch of lies. I have never done anything that is not consensual. Someone is trying to ruin me, my business, my family and I need to find out who that is.''
Weinstein must have been happy with the meeting and the material Stella and her team subsequently produced. The former head of Miramax went on to spend more than £1million with Black Cube to protect his reputation.
Stella sees her efforts as a professional job aimed at protecting her client. Some of those at the other end of Black Cube's techniques, however, describe a sinister and complex web designed to ensnare and cripple those fighting him.
Key witnesses have had their reputations badly damaged since the Weinstein allegations first surfaced, while journalists working on the story have been intimidated.
Ronan Farrow, the writer who broke the Weinstein story, details in his book Catch And Kill how the 67-year-old mogul's intimidation tactics left him so frightened that friends advised him to buy a gun.
He was so certain his calls and emails were being monitored he took to communicating with an encrypted messaging app and only connected to the internet through anonymous wi-fi hotspots.
Farrow was so worried that he asked a rival Israeli spy firm what to do if he was being followed by a Black Cube operative. The man replied: 'Just start running.'
The campaign certainly seems to have been successful. Several high-profile cases against Weinstein, including those by actress Ashley Judd and Hollywood producer Lucia Evans, have been struck out.
Weinstein's legal team, led by Donna Rotunno, nicknamed the Bulldog, are confident of getting their client off when his trial on five counts of sexual assault and rape begins on January 6.
Faced with the prospect of potentially spending the rest of his life behind bars, it is no surprise Weinstein turned to Black Cube to save him. But just how does it operate?
Stella explains that every mission begins with a team brain-storming session, but that the field operative always has the final say.
'You are involved in the think-tank process. No one is going to tell you to be a brain surgeon if you cannot hold that cover,' she adds.
'The team builds the operation and does the analysis and research, and the psychologists build the psychological profile of the person you are supposed to meet.
'Then they bring in the agent, present them with different options and see what works best.'
Recalling her approach to Rose McGowan using the identity Diana Filip, Stella says: 'At that point it was just another cover. It has to be really in-depth, you have to know the role really well and the character really well. Essentially it is all just theatre, right?'
The former agent does not appear to recognise that her approach may have been immoral.
Indeed, during a two-hour interview, Stella only betrays her discomfort once and that is when she is asked what she would think of someone approaching her daughter in the same manner that she approached McGowan.
After a jarringly long pause, the former field agent calmly recovers her equilibrium and says: 'You are not meeting them in order to do anything wrong or harmful to them… in 99 per cent of projects I reveal the bad guys.'
When asked whether this was true in the Weinstein case, she confidently replies: 'Me talking to someone is not harmful. I am just extracting information.'
McGowan, however, was distraught to discover that a woman she regarded as a friend was actually an agent working for Weinstein.
'Everyone lied to me all the time,' she said later.
'I've lived inside a mirrored fun house.' She is now suing Weinstein and Black Cube over what she describes as an attempt to smear and defraud her.
So was Stella acting during her 'friendship' with the actress? 'In a lot of aspects we are very much alike, so the connections were very real,' she says, seemingly unable to comprehend why her actions would appear distasteful to most people.
'In a parallel universe, in a different dimension, in different circumstances, we really could have been friends because although the circumstances were… a lie… the human aspect was very authentic.'
Stella claims that her traumatic childhood in war-torn Sarajevo gave her the ability to have empathy for her targets like McGowan.
'The only way I can get to people and get into their heads is by empathy and you cannot fake that. The empathy is real even if the circumstances are tricky.'
But no matter how many mental blocks she has put up to rid herself of any feelings of guilt, there is no doubt her actions with McGowan were truly questionable. And she was not the only one in the Black Cube cast of actors.
Briton Seth Freedman, a one-time Guardian journalist and a former equities broker, who spent time in the Israel Defence Forces, told The Mail on Sunday that he, too, was tasked with 'finding out who was talking to the press'.
Freedman had some success with McGowan. He used the cover story of being a journalist working on an article about Hollywood to convince McGowan's literary agent to encourage the star to speak to him.
There followed a 75-minute call in which she believed she was talking to a concerned British journalist and revealed information about her accusations against Weinstein.
Freedman denies he was involved in any black ops against Weinstein's victims.
'The line that is always used is Black Cube are hired to investigate, harass and silence victims,' he says. 'I wasn't hired to do any of these things.'
Just like Stella, Freedman was unmasked by Farrow and no longer works for Black Cube.
Stella claims she left the firm in June for personal reasons.
'Being a mother changed my priorities, the risk assessment, everything,' she says.
'You cannot do the job with small children. The universe sends you clues and that was mine.'
So what would she say to McGowan today?
'I think she is very brave, very strong, and I am very supportive of what she was doing,' she says, smiling.
'I am sorry if she ever felt betrayed or hurt by anything that I had to do. I am sorry that I was another person in her life that was there under false pretences. My goal was never to hurt her.'
As with everything she says over the course of the interview, it is impossible to tell whether the trained spy is lying or not.
Regardless, it is perhaps a little too late for apologies.
Mr Weinstein's attorneys said in a statement: 'Mr. Weinstein had a right to examine any claims against him to attempt to prove they were false, as anyone facing false allegations would do.
'The firm is a recognized investigative agency that was referred by the largest law firm in the world devoted solely to business litigation and arbitration. In addition, the research that was done was more comprehensive than so much of the fiction dreamed up for [Ronan Farrow's] book.'